Data Breaches 101: What They Are And How To Prevent Them
VISTA InfoSec
FEBRUARY 25, 2024
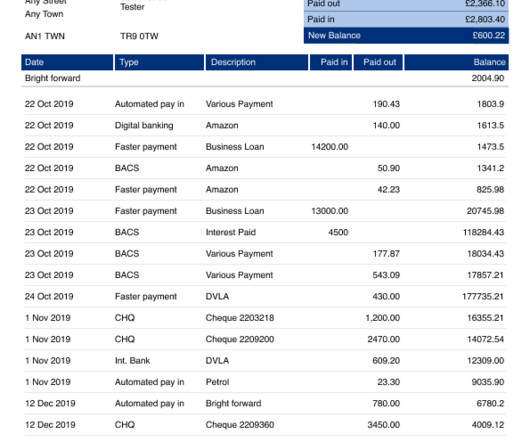
Virtually every industry faces data breach risks today as sensitive information gets digitized and networked across cloud platforms. But some data types see higher breach rates than others.

















Let's personalize your content