Essential Guide to Seamless CCaaS Implementation
VISTA InfoSec
OCTOBER 21, 2024
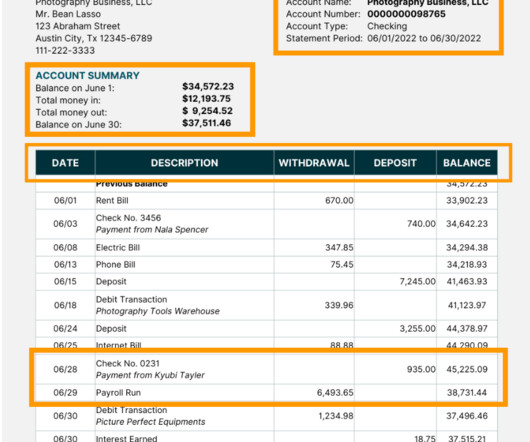
Hence, it’s essential to assess the following factors when deciding: Customization: The platform should allow for tailored solutions that meet the unique needs of your business. Authentication: Implement multi-factor authentication (MFA) to add an extra layer of security to your system.


















Let's personalize your content