What is the Most Frustrating Experience in SOC 2 Audit and Attestation?
VISTA InfoSec
OCTOBER 21, 2024
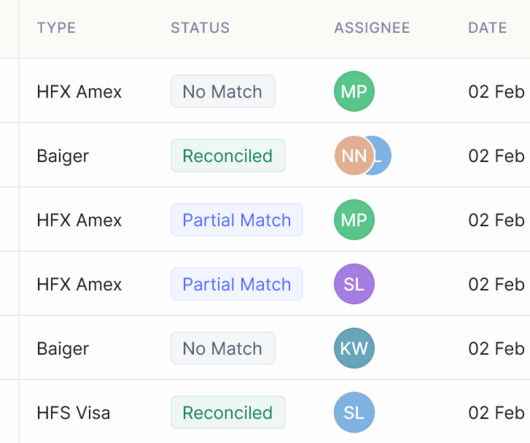
The SOC 2 (Service Organization Control 2) audit and attestation process is something that has been devised by the American Institute of Certified Public Accountants (AICPA) in order to ensure that organizations which provide services have secure procedures to govern data so as not to compromise the welfare of their clients.
















































Let's personalize your content