Strengthening Cyber Defenses with Multi-Factor Authentication
VISTA InfoSec
NOVEMBER 7, 2023
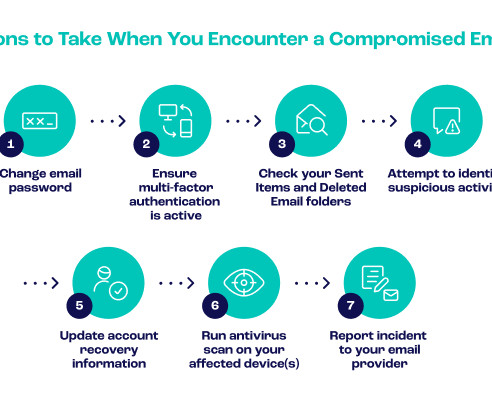
Mutli-Factor Authentication (MFA) isn’t a new concept. What Is Multi-Factor Authentication? Let’s start with another simple definition – multi-factor authentication is any authentication method where more than one criterion has to be satisfied before access is granted to digital assets.















































Let's personalize your content