Digital Identity Verification
Segpay
NOVEMBER 26, 2024
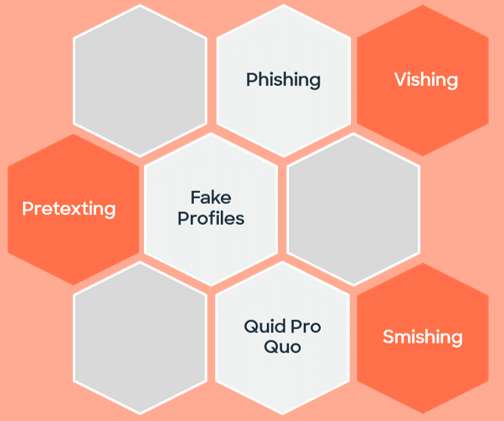
In today’s digital world, online ID verification has become a crucial component of customer onboarding. As we move our personal, financial, and governmental interactions to digital platforms, the need for reliable and efficient digital identity verification processes has become critical. What is Digital Identity Verification?














































Let's personalize your content