Mastercard Deploys Generative AI to Enhance Compromised Card Detection
Fintech News
MAY 22, 2024
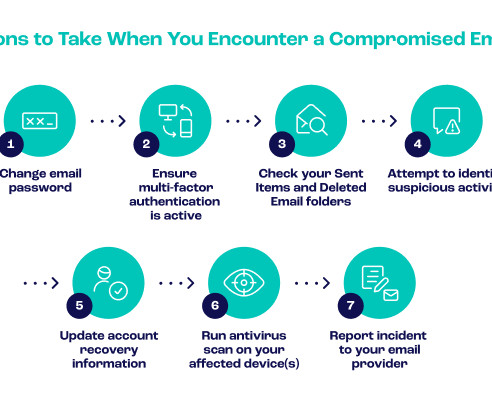
Mastercard has announced the implementation of generative AI technology to significantly accelerate the detection of compromised cards, enhancing protection for cardholders and securing the payment ecosystem. Furthermore, it has increased the speed of identifying at-risk or compromised merchants by 300%.














































Let's personalize your content