How to Use the Terraform Destroy Command to Control Cyber Attack Damage
VISTA InfoSec
MAY 23, 2024
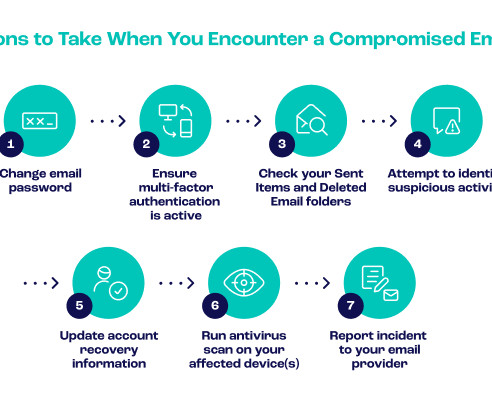
To do this, the specific resource has to be identified by running the “plan” command and then editing the configuration file to remove the block that defines the resource targeted for deletion. These storage resources can be compromised and lead to data leaks similar to the unsecure S3 bucket of THSuite reported in 2020.



























Let's personalize your content