Understanding the Cyber Risks in Video Communication
VISTA InfoSec
JUNE 19, 2024
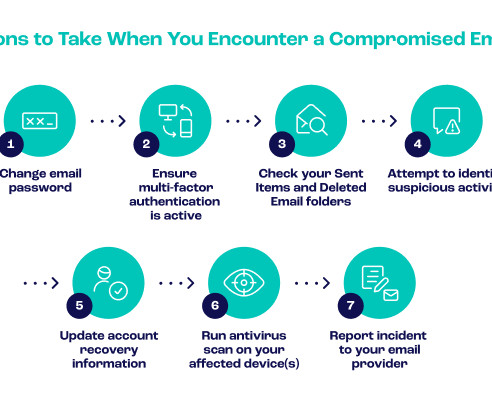
For instance, an attacker might send an email that appears to be from a trusted video communication platform, prompting you to click on a link to verify your account or update credentials. Additionally, consider platforms with strong access controls, such as multi-factor authentication (MFA) to prevent unauthorized access.













Let's personalize your content