IBM upgrades mainframe to speed data encryption
Payments Source
JULY 17, 2017
Credit card or personal data transactions getting processed through IBM equipment will soon benefit from "one-click" data encryption in a powerful new mainframe.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
 Data Encryption Related Topics
Data Encryption Related Topics 
Payments Source
JULY 17, 2017
Credit card or personal data transactions getting processed through IBM equipment will soon benefit from "one-click" data encryption in a powerful new mainframe.

Payments Source
SEPTEMBER 2, 2019
Many companies have tools in place alerting them to possible security issues, but if companies get a large volume of issues, this quickly overwhelms the ability for security and risk professionals to analyze, prioritize, and remediate, writes DivvyCloud's Chris DeRamus.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

VISTA InfoSec
MARCH 13, 2025
Protecting cardholder data: Encrypting sensitive data during transmission. Implementing strong access control measures: Limiting access to cardholder data based on job responsibilities. Maintaining a vulnerability management program: Regularly updating anti-virus software and conducting vulnerability scans.
The Fintech Times
NOVEMBER 28, 2024
” Security stands at the forefront of Samsung Pay’s design, incorporating state-of-the-art features such as fingerprint recognition and advanced data encryption to safeguard users’ sensitive information.

Payments Source
DECEMBER 12, 2019
In updating its point-to-point encryption standard, the PCI Security Standards Council says the resulting simplified validation process for component and software providers will result in more products available for cardholder data protection.

The Paypers
JULY 31, 2024
Accenture and SandboxAQ have announced an expanding partnership to help strengthen data encryption for enterprises and protect against future threats.

VISTA InfoSec
APRIL 5, 2024
The aftermath of a data security concern could change the landscape of your business, depending on the incident. Cybersecurity measures such as data encryption, two-step verification, and stringent policies on data access are some of the things that should be implemented in order to minimize online threats.

Fintech Finance
NOVEMBER 27, 2024
while protecting customers through tools like strong customer authentication (SCA), 2-factor authentication, and PCI DSS data encryption.

Fintech Finance
FEBRUARY 20, 2025
Data Encryption & Secure Storage: Ensure sensitive information and API keys remain protected with leading cloud encryption technologies. Distributed denial of service (DDOS) protection ensures all traffic is protected from malicious threat actors.

The Paypers
JANUARY 19, 2021
US-based identity management provider Entrust has acquired multi-cloud data encryption, key management, and cloud security posture management solutions provider HyTrust.

VISTA InfoSec
JUNE 18, 2024
Ultimately, encrypting sensitive data, whether stored or transmitted, is a critical safeguard. Implement comprehensive data encryption practices to strengthen your defenses against data theft and exposure. Implement Strong Access Controls Keeping prying eyes away from sensitive data is crucial.

VISTA InfoSec
FEBRUARY 25, 2024
Secure Passwords Enforce complex password requirements, password manager usage, frequent rotation policies, and supporting infrastructure across all accounts with access to sensitive data.

Basis Theory
NOVEMBER 12, 2024
The ciphertext is a computed value, based on a key and plaintext data. To retrieve the original sensitive data within the ciphertext, you’ll need to use a key capable of converting the ciphertext data back into plaintext data. Encryption and tokenization are more different than they are similar.

Fintech Finance
NOVEMBER 27, 2024
Security stands at the forefront of Samsung Pay’s design, incorporating state-of-the-art features such as fingerprint recognition and advanced data encryption to safeguard users’ sensitive information.

The Fintech Times
MAY 23, 2024
Leveraging technologies like advanced data encryption, the company aims to power faster digital payments and help advance the UAE’s cashless economy. “We This means Comera Pay can now launch payment solutions that provide simpler, more secure transactions for merchants and consumers.

Payments Source
APRIL 5, 2016
A data encryption method that Heartland Payment Systems CEO Robert Carr swears by has received high-level acceptance as part of a new standard.

Payments Source
MAY 3, 2016
After planting its roots firmly in data encryption and enterprise content management for Payment Card Industry security compliance, Hyland has turned its attention toward fraud detection.

VISTA InfoSec
APRIL 28, 2024
Installing and maintaining a firewall configuration to protect cardholder data. Protecting stored cardholders’ data. Encryption of cardholder’s data across all networks. Refrain from using vendor-supplied defaults for system passwords and other security parameters.

Fintech Finance
JULY 3, 2024
It will be seamlessly integrated and operate with high levels of security, ensuring that customer data is protected while enhancing their payment experience. Trustly uses data encryption in transit and customer banking details are never stored to improve security.

EBizCharge
JANUARY 14, 2025
Data encryption is crucial for a payment gateway since it converts sensitive information, like credit card details, into a secure format to prevent unauthorized access during online payments. FAQs regarding payment gateways FAQs regarding payment gateways What security features do payment gateways offer?

The Payments Association
SEPTEMBER 27, 2024
In 2022, the company received a patent for another piece of AI, their Secure Lockbox , which features pioneering homomorphic data encryption. This patent enables Lucinity to encrypt all personally identifiable information (PII) while still using PII as an input into AI in its encrypted form.

Stax
MARCH 13, 2025
Card networks must maintain them properly and pay for fraud prevention tech (data encryption, tokenization, real-time tracking, etc.). Keep card networks up and running Large, global infrastructures are required to process massive volumes of transactions safely and efficiently.

FICO
NOVEMBER 1, 2016
Data encryption. The NYDFS requires data encryption not just for data in-transit but also for data at-rest. The NYDFS proposal requires multi-factor authentication for any users accessing internal systems from an external network and for privileged access to database servers.

Segpay
FEBRUARY 21, 2024
Secure Data Encryption: Generative AI contributes to the development of secure data encryption methods. By leveraging advanced encryption algorithms, organizations can protect sensitive information, ensuring that the data remains unreadable and unusable even if unauthorized access occurs.

VISTA InfoSec
SEPTEMBER 25, 2024
Some best practices to ensure robust cybersecurity include: Data Encryption: All sensitive data should be encrypted both in transit and at rest to prevent unauthorized access and ensure efficient data security measures.

VISTA InfoSec
OCTOBER 21, 2024
Some best practices to ensure robust cybersecurity include: Data Encryption: All sensitive data should be encrypted both in transit and at rest to prevent unauthorized access and ensure efficient data security measures.

The Paypers
NOVEMBER 14, 2016
(The Paypers) WISeKey has teamed up with Wellness Telecom to integrate and install its authentication data encryption and IoT cryptographic chip into millions of Wellness Telecom’s IoT devices.
NFCW
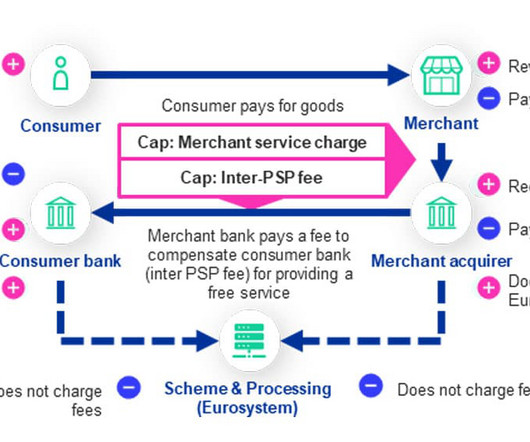
JUNE 25, 2024
“The Eurosystem would use state-of-the-art measures, including pseudonymisation, hashing and data encryption, to ensure it would not be able to directly link digital euro transactions to specific users.”

Fintech News
APRIL 22, 2024
Finally, SecIron understands the importance of data privacy. To ensure user financial information remains protected at all times, data encryption scrambles sensitive data within mobile applications. This proactive approach ensures businesses stay ahead of constantly evolving cyber threats.

PYMNTS
FEBRUARY 21, 2019
Security and technology consulting company Accutive is rolling out a new solution designed to give enterprises an alternative to data encryption to protect sensitive information. 20), Accutive said it is launching its Data Discovery and Data Masking solutions. In a press release on Wednesday (Feb.

PYMNTS
JUNE 27, 2017
Wealthy countries with developed financial and payment infrastructures are most likely to have their data encrypted and held for ransom by cybercriminals, according to a recent report by global cybersecurity company Kaspersky Lab. In 2016-17, cyber attackers have set their sights on mobile users in the U.S.,
The Finance Weekly
JUNE 5, 2024
Facilitate data-sharing with stakeholders using APIs, ETL connectors, and built-in integrations. 8) Security Top-tier security and compliance measures, including BYOK, role-based access control, user management, SSO support, and data encryption at rest.

Fintech Finance
MAY 23, 2024
Leveraging cutting-edge technologies like advanced data encryption, Comera Pay aims to power faster digital payments and help advance the UAE’s cashless economy. “We With this approval, Comera Pay is now equipped to launch innovative payment solutions that will provide a simpler, more secure transactions for merchants and consumers.

The Finance Weekly
DECEMBER 30, 2021
To prevent harm to your network and mitigate risk, consider requiring multi factor authentication to access company data, encrypting email, securing email attachments, and implementing other best practices. Malware attacks, especially ransomware attacks, are on the rise.

PYMNTS
JUNE 5, 2019
Data encryption will be possible both at rest and in transit. CryptoKit is a new Swift framework that makes it easier and safer than ever to perform cryptographic operations, whether you simply need to compute a hash or are implementing a more advanced authentication protocol.”.

The Fintech Times
OCTOBER 25, 2024
The combined solution from Ripple Custody and IBM enabled the bank to securely build, deploy and manage institutional-grade key management infrastructure with end-to-end security to protect private keys, applications and data.

EBizCharge
MARCH 18, 2025
By adhering to these standards, businesses can reduce data breach risks and maintain regulatory compliance. Tokenization and encryption: Tokenization replaces credit card details with unique tokens with no exploitable value, preventing hackers from accessing sensitive data.

EBizCharge
JANUARY 21, 2025
Secure payment processing: Data encryption ensures that credit card details and payment data are secure, reducing fraud risk. CNP transactions: Virtual terminals can process payments without the card physically being present, which is ideal for phone or online orders.

Stax
FEBRUARY 19, 2025
Security & compliance Security is a top priority, especially when dealing with sensitive customer data. When selecting an ISV partner, businesses should verify: Data encryption standards to prevent breaches. Compliance with industry regulations , such as GDPR for data protection or PCI DSS for payment security.

Exact Payments
JULY 1, 2024
The layer of defense WAFs provide is crucial in maintaining the integrity and security of the data pipeline. Data Encryption and Management Sensitive pieces of PII are encrypted with unique keys as soon as our APIs index them. The encrypted data is then written to our database.

Fintech Finance
JULY 1, 2024
The Eurosystem would use state-of-the-art measures, including pseudonymisation, hashing and data encryption, to ensure it would not be able to directly link digital euro transactions to specific users.

The Fintech Times
APRIL 14, 2024
In addition, the retention portal offers secure access, multiple layers of data encryption, multi-factor authentication, and regular security audits to create a fully comprehensive and secure solution. It also offers customers the ability to self-select a convenient date to switch products and pay any outstanding fees when applicable.

EBizCharge
NOVEMBER 27, 2024
Data encryption: Data is encrypted and sent to the payment processor. The approval or decline is then sent back through the payment gateway to the online merchant, alerting them to complete the order or notify the customer of payment issues. Authorization request: The processor communicates with the bank for approval.

Stax
FEBRUARY 26, 2024
Because the transaction takes place through a payment gateway that utilizes data encryption or tokenization to secure sensitive information during transmission, accepting payments using a virtual terminal from Stax (which is PCI compliant) is secure. Learn More What Is a Contactless Virtual Terminal?
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content