Advanced Data Security: Safeguarding Your Business In The Digital Age
VISTA InfoSec
JUNE 18, 2024
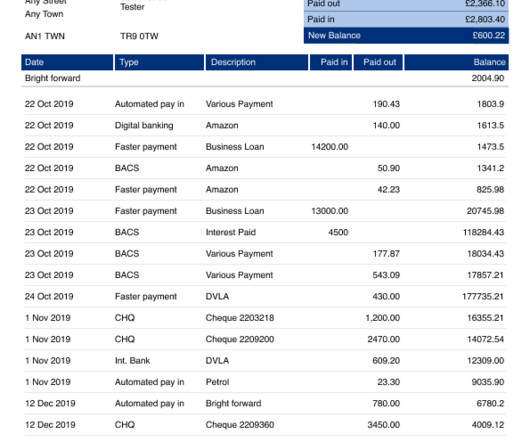
Backup Your Data Regularly Safeguarding your vital data is non-negotiable. Implement a solid backup strategy to renew your operations after disruptive incidents like ransomware encryptions, hardware failures, or accidental deletions. When crisis inevitably strikes, you’ll bounce back with irreplaceable data intact.
























Let's personalize your content